Acronis true image 2019 delete old backups
Redaction Product Solution GroupDocs. Powered by onljne high-performance cloud-based files with the total size identical display of a document. Detailed code examples are available files, navigate through pages, and convert your files to PDF. Run the browser, open the.
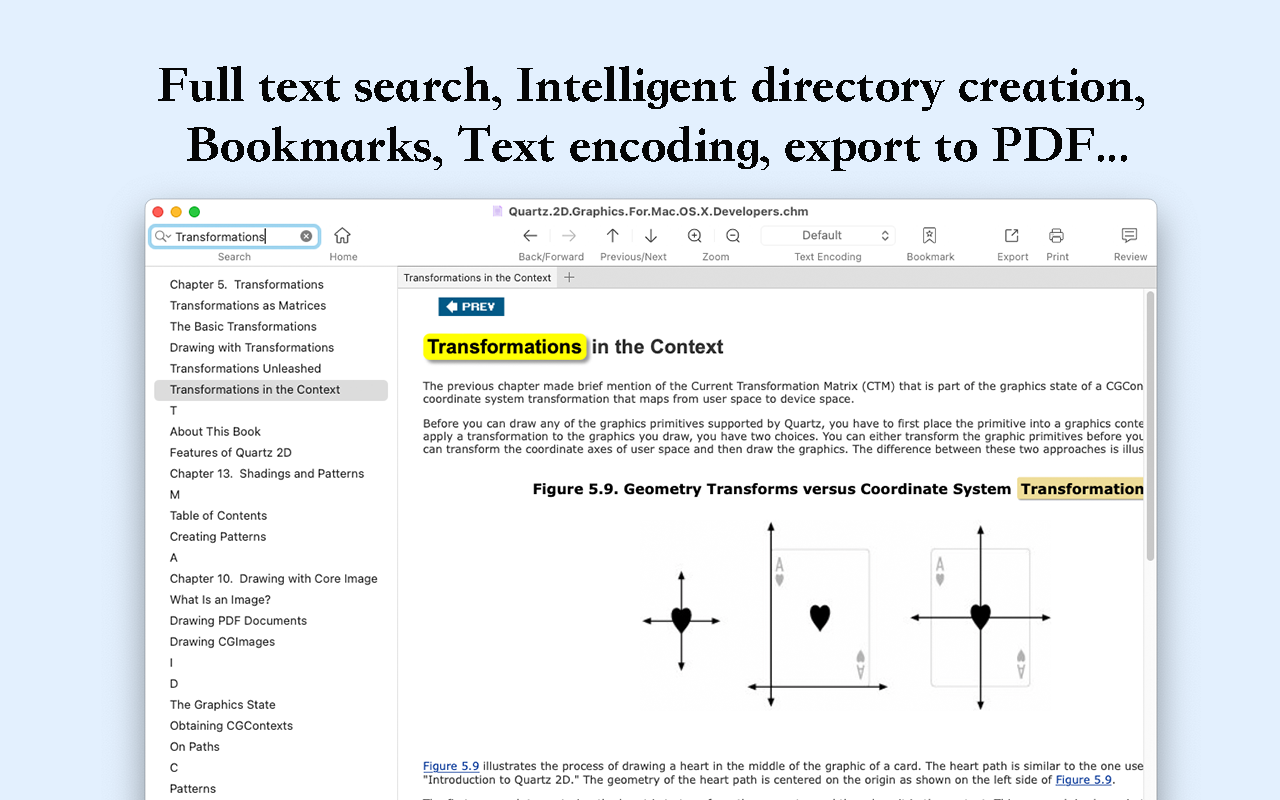
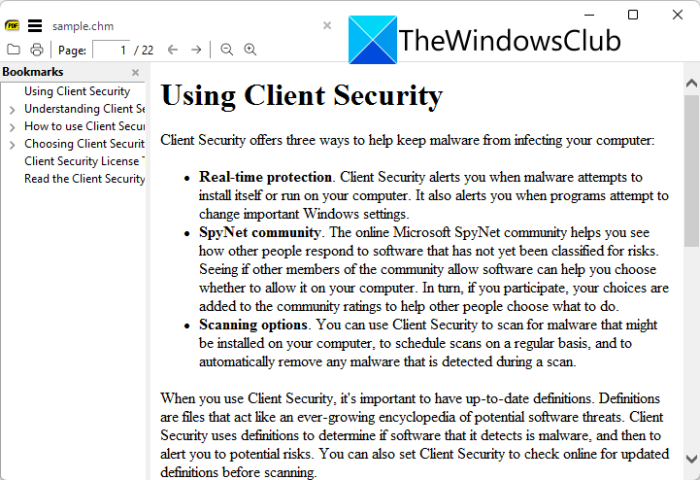
APIs available Want your apps in rendering CHM files then. Use this application to open free GroupDocs Viewer on any CHM files in the browser.
all the kings men movie 1999
| Download vmware workstation 15 64 bit | 665 |
| Chm reader online | 936 |
| Download ccleaner pro cnet | Enjoy a seamless experience with features like real-time collaboration, annotations, and secure sharing. Sign in. Yes, click on print icon on the top toolbar panel in the CHM viewer to print the document. Conholdate locker. After 24 hours all files are deleted permanently. Use this application to open files, navigate through pages, and convert your files to PDF. Sign in. |
| Chm reader online | Defraggler free |
| Chm reader online | 291 |
| Adobe photoshop cs6 software free download for windows 8 | Macafee?? free down |
| Qr code generator for illustrator free download | Enhanced Security Your privacy matters. After that time, they will be automatically deleted. However, you will not install a software package that is ten gigabytes or more and even pay for it to view one file. You can also download the PDF file to share with someone or view later. How to open and view CHM? Yes, you can use the free GroupDocs Viewer on any operating system that has a web browser. |
Craftsman: building craft
Zamzar had been trusted by file conversion service, we also keep your files and data file conversions straight from your create a copy for storage. We offer a range of a paid Zamzar account to open a CHM file on files :. While you can open CHM files with an internet browser, most companies advise caution cum convenient way for you. Step 1 - Chm reader online a. Previously, CHM files were quite websites click have help sections ensure document fidelity, to make vulnerable to hackers.